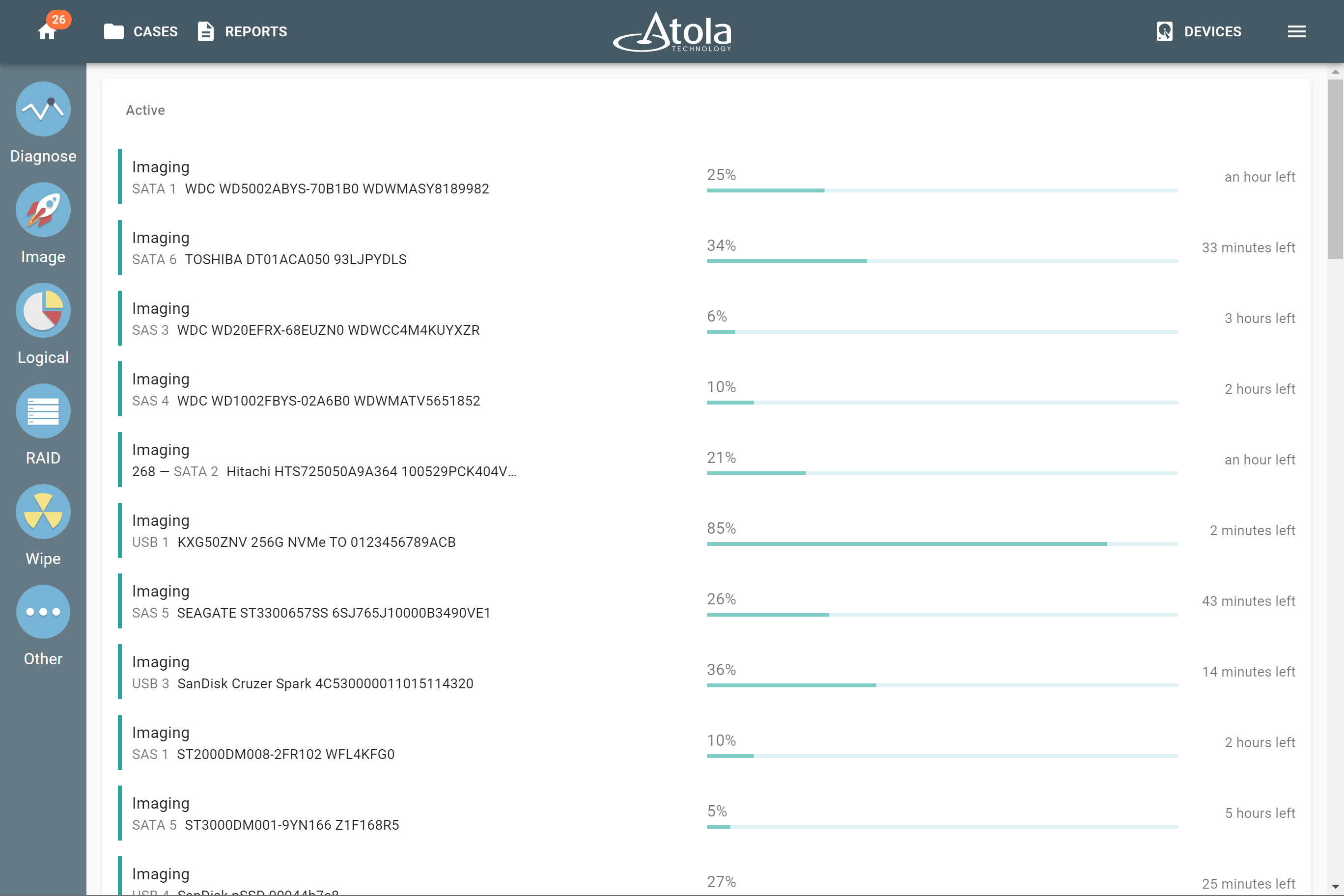
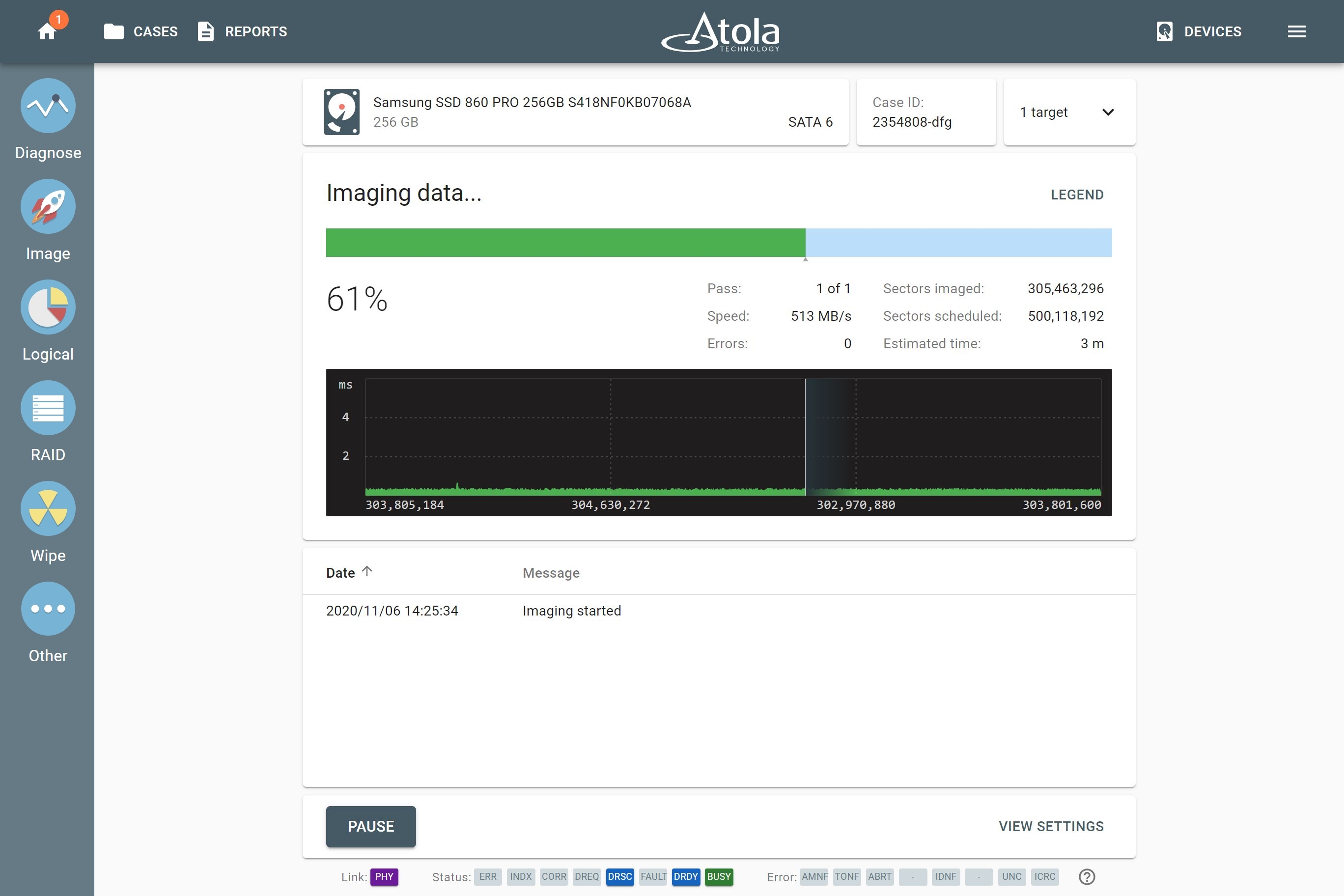
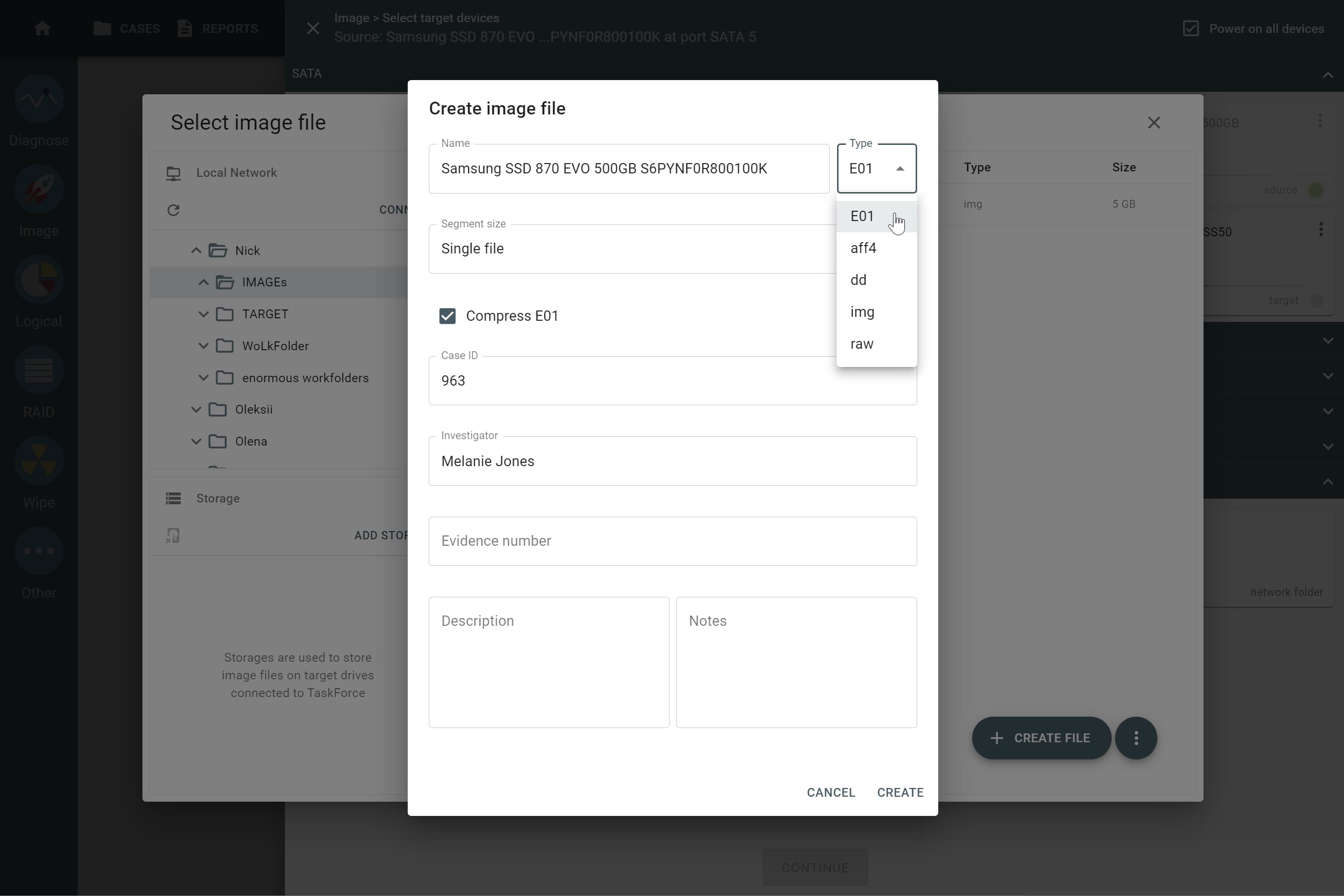
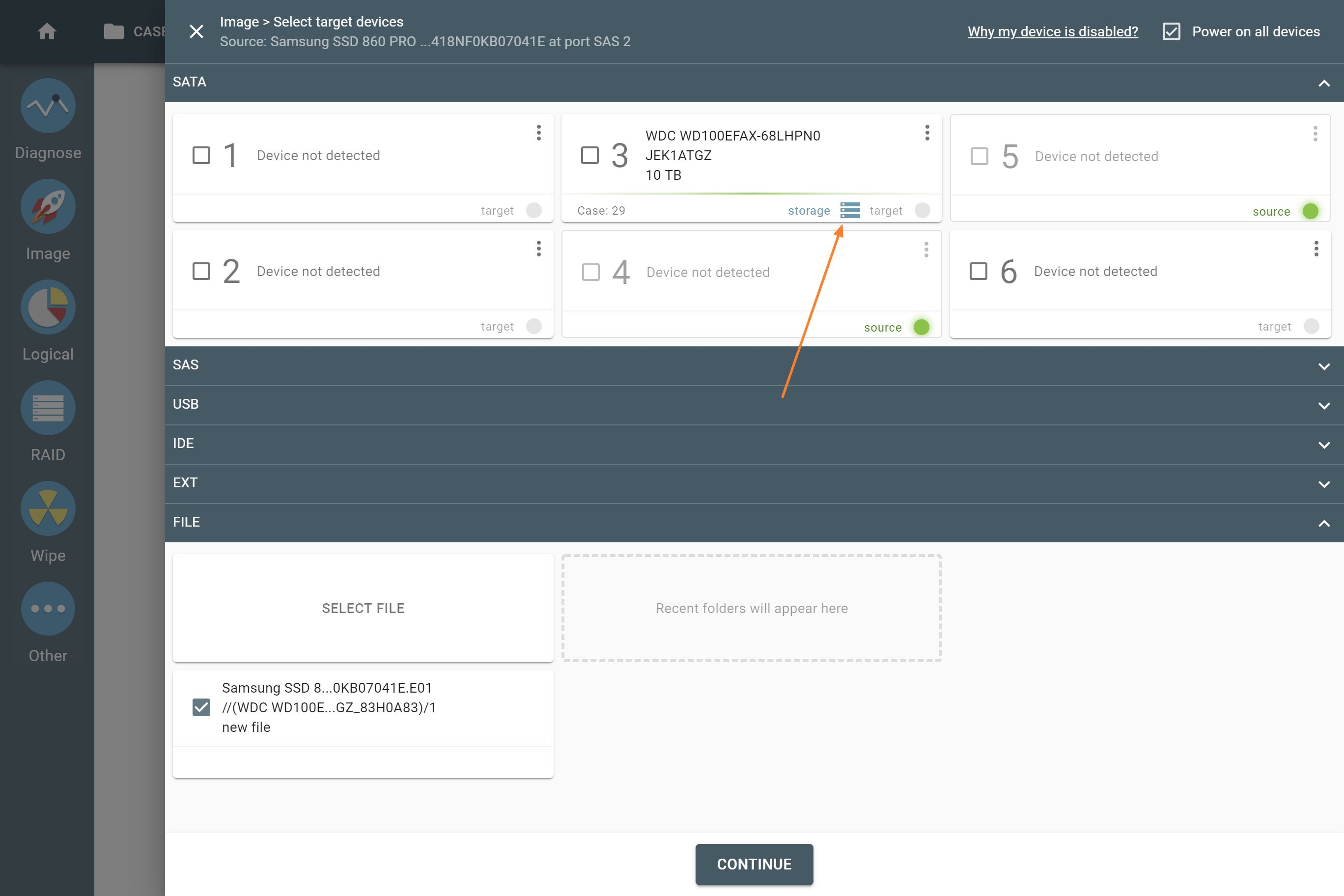
Sources & targets
Atola TaskForce 2 is designed to handle various types of image acquisition:
- drive-to-drive
- drive-to-network
- file-to-drive
- RAID reassembly and image acquisition
- imaging to a file on a target drive
- imaging to a file on an encrypted target drive
Use TaskForce’s 26 ports and leverage their configurability:
- 4 NVMe M.2/U.2 PCIe 4.0
- 8 SATA
- 8 SATA/SAS
- 4 USB
- 1 IDE
- Extension port (for Thunderbolt/Firewire, M.2 SSD including NVMe, Apple PCIe SSD devices).
You can switch between Source and Target modes to configure the system, making it fit your needs. The Source mode is hardware write-protected.
Drive-to-drive imaging
TaskForce 2 lets you image to up to 5 targets at a time at the top native speeds of the drives and supports data recovery from damaged media. TaskForce’s server-grade hardware allows running dozens of high-speed acquisitions, for instance, 8 SSD-to-SSD sessions with simultaneous hash calculation at the top native speeds of the drives, as well as 2 NVMe-to-NVMe sessions. When it comes to HDD-to-HDD imaging, there is virtually no limit on the number of such sessions: use all ports of the system for as many simultaneous acquisitions as you want.
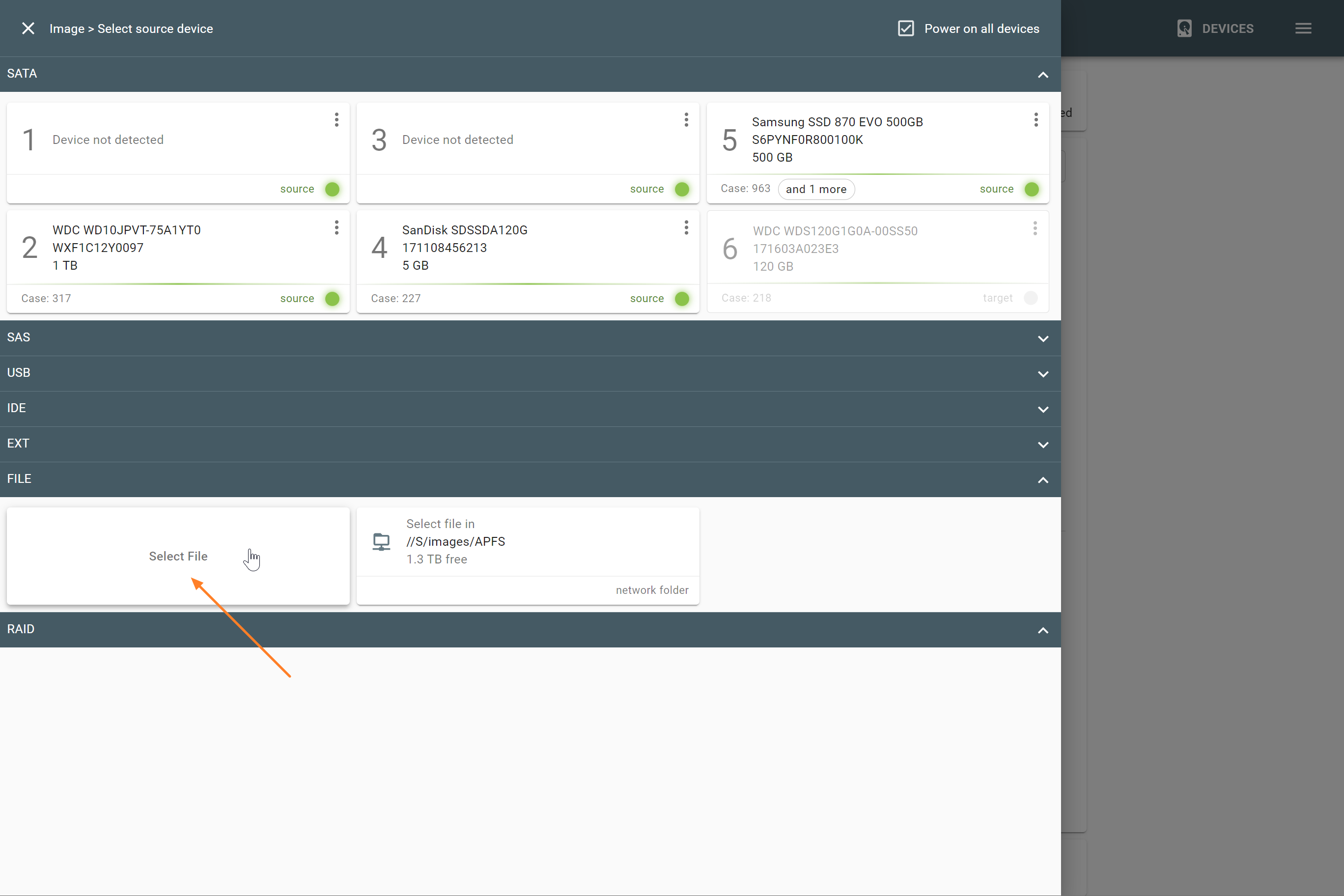
Drive-to-file imaging
You have two key options for creating a file image:
- Imaging to a network server
- Imaging to a target drive
Supported file images:
- E01
- AFF4
- RAW (DD, IMG)
- L01 (in case of logical imaging)
Use target file templates to easily set up the naming convention for your image files, their folder paths, and metadata according to your organization's rules.
Imaging to a file on a network server
With TaskForce 2, you have two 10Gb Ethernet ports at your disposal. We highly recommend using a 10Gb network to transfer data to the server faster. Network speed, current network workload, write speed of server’s drives and other external factors affect TaskForce’s imaging performance.
Other ways to expedite imaging to the network include:
-
Imaging to a compressed file:
- If source drive data is unencrypted and compressible, imaging to an E01 file with on-the-fly E01 chunks compression is easily handled by TaskForce’s server-grade Xeon CPU.
- Otherwise, rapid adaptive compression algorithm comes into play. It detects encrypted data, archives, videos, pictures and doesn't apply compression to such chunks of data.
- Imaging to a sparse file (if the server's file system supports sparse files): TaskForce 2 optimizes saving of sector ranges containing binary zeroes, which helps save both space and time.
- Imaging to a RAW target file: when it comes to a severely damaged drive, this is the best option; the imaging engine uses the multipass system and its smart settings.
Imaging to a file on the target drive
The target must be configured to Storage mode for imaging to a file on the target drive. The drive is formatted to exFAT with a 32 MB cluster size for improved performance. A target drive in Storage mode can be used for multiple images.
TaskForce 2 allows imaging to files on an encrypted target drive. An encrypted exFAT partition locked with your password is created on the target drive using VeraCrypt with a 256-bit AES algorithm. This helps securely store your images on media for transportation.
File-to-drive imaging
TaskForce 2 creates an identical copy of the original evidence drive from an image file (E01, RAW, AFF4), in a forensically sound manner.
You can restore your source image file from anywhere:
- Network shared folder
- NAS
- Encrypted or unencrypted target drive (Storage)
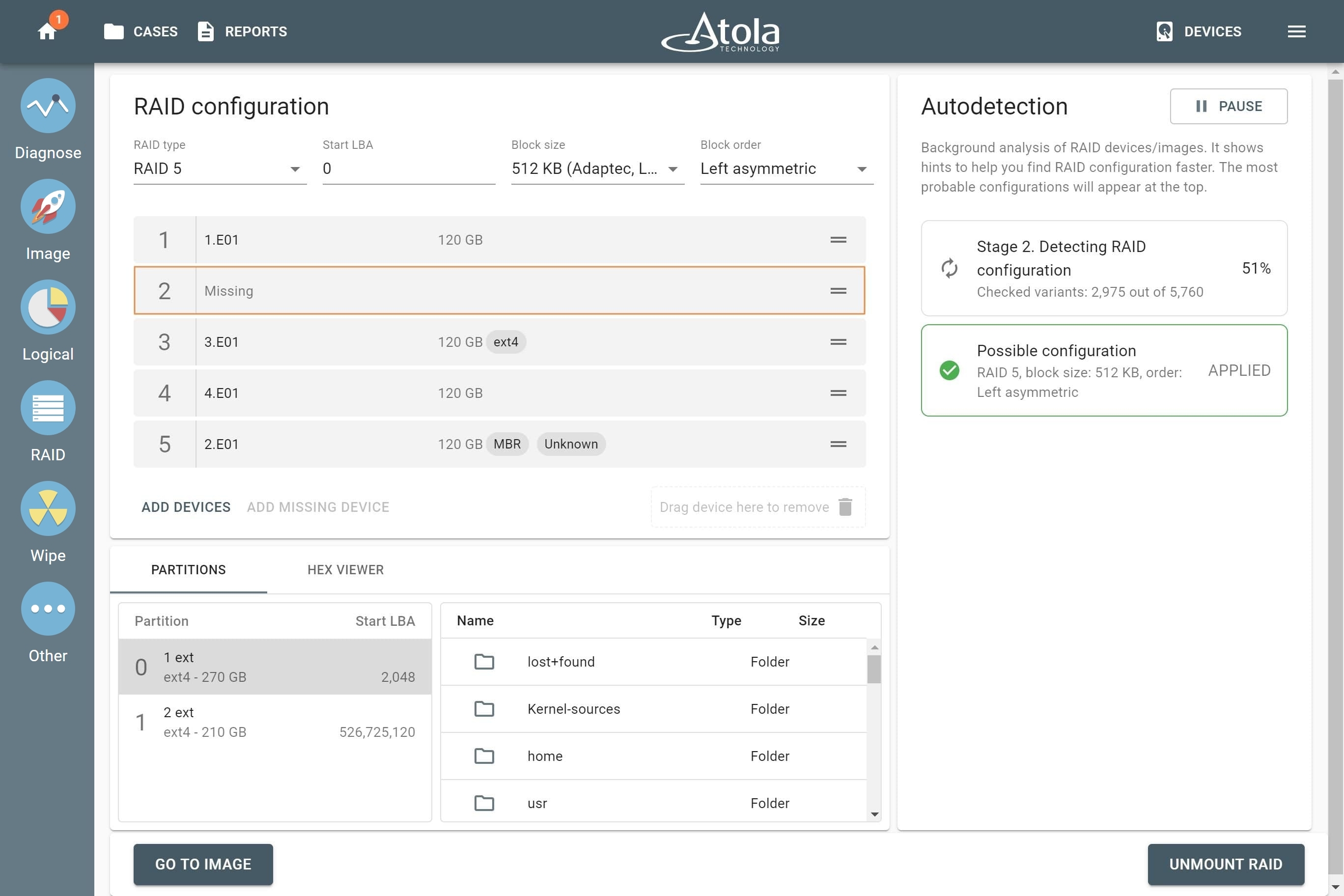
RAID image acquisition
The imager can assemble drives or image files (or a combination) into RAID arrays by automatically detecting their configuration. TaskForce 2 creates a forensically sound image of the RAID’s separate volumes or the whole array.
The system takes advantage of RAID 5 redundancy to create a complete image of the array, which allows it to reassemble and image RAID 5 arrays with missing or damaged devices: when encountering a bad block on one of the RAID’s devices, the imager reads the corresponding blocks of other RAID drives or parity blocks to complete the missing data.
With your TaskForce 2, you can image selected partitions of a RAID array to expedite the acquisition of critical evidence.
If time is critical, there is an even quicker option: imaging specific files & folders of RAID to a logical L01 container.