Web API for Workflow Automation
Automation of the digital forensic process becomes not just relevant but increasingly pressing to examiners dealing with ever growing volumes of data in forensic cases.
To enable TaskForce 2 users to integrate their forensic disk imaging system into their automated workflow, we provide the ability to launch, track and stop operations via Web API.
API (application programming interface) helps external software to communicate with TaskForce 2. It prescribes the type of commands that can be sent to TaskForce, describes the behavior TaskForce 2 should demonstrate and the type of responses it should send back to the automation software.
TaskForce 2 API is based on HTTP requests and JSON-encoded responses. See API specification.
To understand how it can be used to communicate with TaskForce 2, please see the examples below.
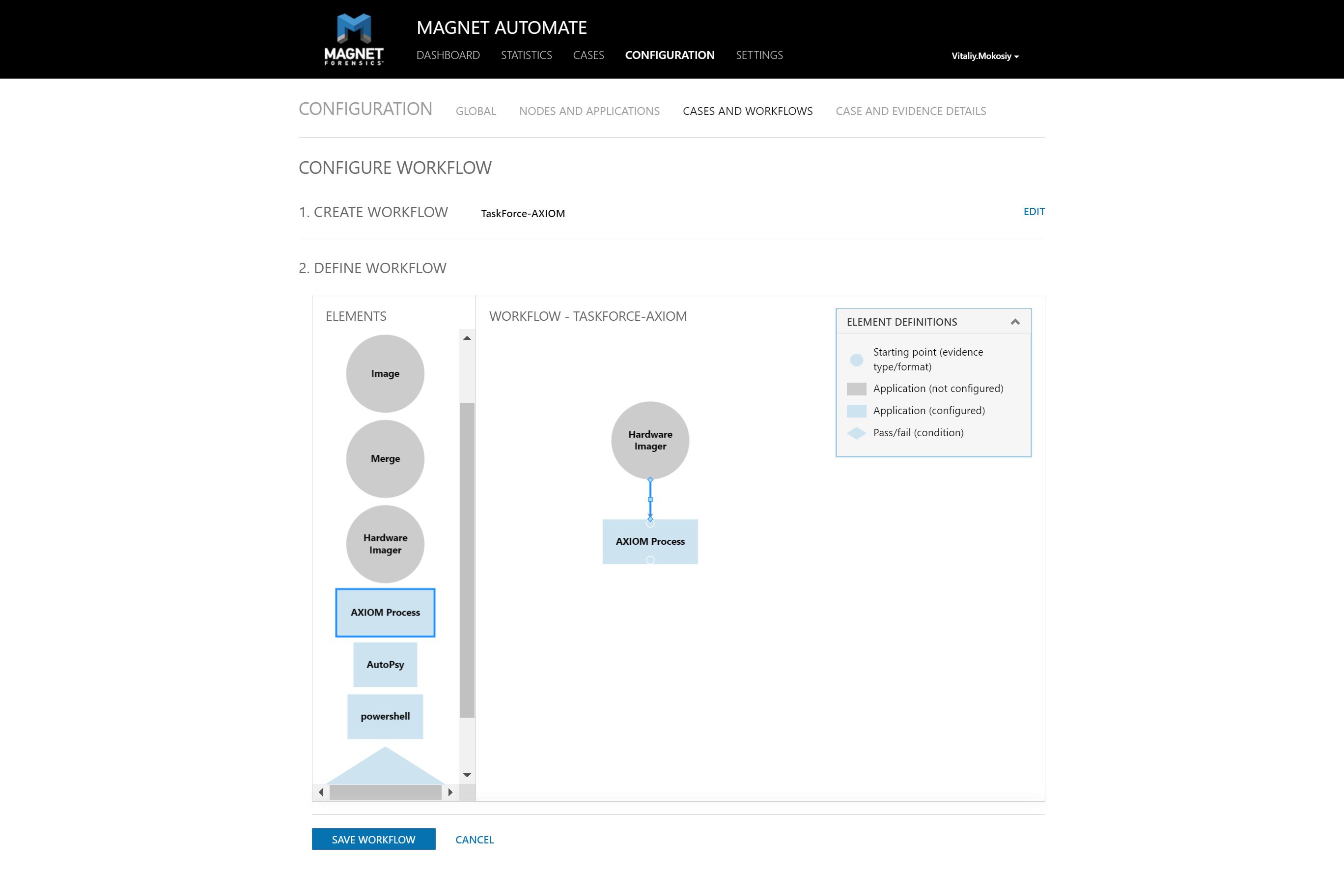
Integration into Magnet AUTOMATE
In Magnet AUTOMATE a user creates a repeatable workflow for each particular type of investigation and saves it as a pattern to operate in the future. Automation eliminates downtown between forensic disk imaging, analysis and other operations included in the workflow.
With TaskForce 2 integrated into the workflow via Web API, Magnet AUTOMATE starts and controls the imaging progress on multiple drives. Later it launches the subsequent analysis of multiple images in parallel. It significantly boosts evidence processing speed.
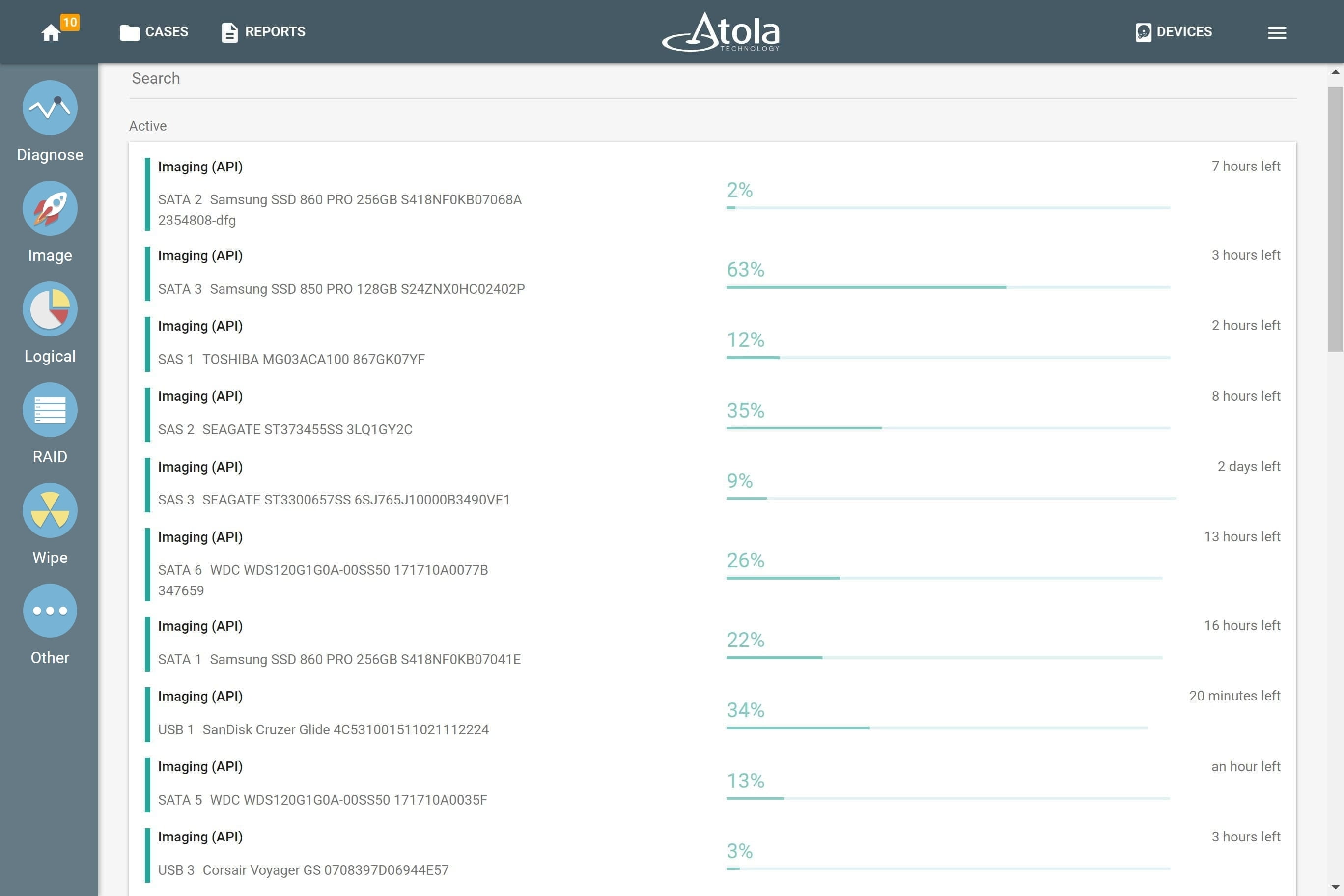
Starting imaging of all available source drives plugged into TaskForce 2
In this scenario, all 16 of TaskForce’s SATA and SAS ports are switched to Source mode and source drives are plugged into them. The system instantly launches 16 imaging sessions using Web API. It is simplified version of Express mode which is already built-in to TaskForce 2.
Python script utilizes /start-image API request and prints task keys of all started imaging sessions.
import sys
if sys.version_info[0] < 3:
raise Exception("Please use Python 3 to run this script")
import urllib.request
ports = ["SATA1", "SATA2", "SATA3", "SATA4", "SATA5", "SATA6", "SATA7", "SATA8",
"SAS1", "SAS2", "SAS3", "SAS4", "SAS5", "SAS6", "SAS7", "SAS8"]
tasks = []
errors = {}
for port in ports:
try:
res = urllib.request.urlopen("http://10.0.0.4/api/start-image?source=%s&targetFolder=//Server/Share" % (port))
tasks.append(res.read().decode('utf-8'))
except urllib.error.HTTPError as e:
errors[port] = e.read()
print("IDs of started imaging tasks:")
print('\n'.join(tasks))
Automatic file analysis upon completion of forensic imaging
By sending /check-task API requests to TaskForce forensic imager, you can track the status of the running imaging sessions. TaskForce 2 returns a report about the imaging progress allowing you (or your code) to find out when the task is completed. Upon receveing this notification, the automation tool launches the forensic analysis of the target image. The Powershell script below demonstrates how this automation flow can be created:
try {
$r = Invoke-WebRequest "http://10.0.0.65/api/start-image?source=SATA4&targetFolder=\\Server\Share"
}
catch {
Write-Output "$($_.Exception.Message)"
exit $_.Exception.Response.StatusCode
}
$taskKey = $r.Content
do {
$check = (Invoke-WebRequest "http://10.0.0.65/api/check-task?taskKey=$taskKey").Content | ConvertFrom-Json
Start-Sleep -s 1
} while ($check.state -eq "progress")
$windowsPath = "C:\Share\" + ($check.target -replace '[\/]', '\' | Split-Path -leaf)
$caseName = "Case123"
$autopsyArguments = '" --createCase --caseName="' + $caseName + ' --caseBaseDir="C:\Work\Cases"'
+ ' --addDataSource --dataSourcePath="' + $windowsPath + '" --runIngest --generateReports'
Start-Process -FilePath "C:\Program Files\Autopsy\bin\autopsy64.exe" -ArgumentList $autopsyArguments
NB. Autopsy Ingest v4.11 does not work with network file paths from the command line. That’s why this example shows a shared folder located at PC where PowerShell script is executed. Therefore \\Vitaliy\Share points to C:\Share folder.
TaskForce 2 API is based on HTTP requests and JSON-encoded responses. See API specification.