Verifying images of damaged drives with segmented hashing
Unlike the conventional linear hashing, segmented hashing produces not a single hash, but a list of hashes of corresponding LBA ranges of the image saved into a CSV file in this format:
Hash, start LBA, end LBA
By validating all hashes on the list, you can prove that the entire image has not been modified. For more information about this hashing method, see Segmented Hashing.
While this method of hashing has a number of benefits for forensic specialists, among its strongest advantages is its applicability to damaged drives.
For one, this non-linear hashing method allows calculating hashes of the good areas of evidence media, while bad areas that are impossible to read and image, are left out of the calculation.
Secondly, if your acquired evidence image is damaged at some point in the future, with the regular linear hashes you will get a hash mismatch upon verification, and the entire image becomes useless, whereas with segmented hashes only the hash of the damaged segment will become invalid. For example, in the case of a 4TB hard drive, if the default 4GB segment size is applied, one invalid hash will account for only 0.1% of the drive, while the remaining 99.9% of hashes can still be verified.
Verifying segmented hashes
For instance, you have imaged a source drive and calculated its segmented hashes, the CSV file is stored on your computer. Now let's simulate a change of the evidence image to see how Segmented hashing helps us identify the areas, whose integrity has not been compromised.
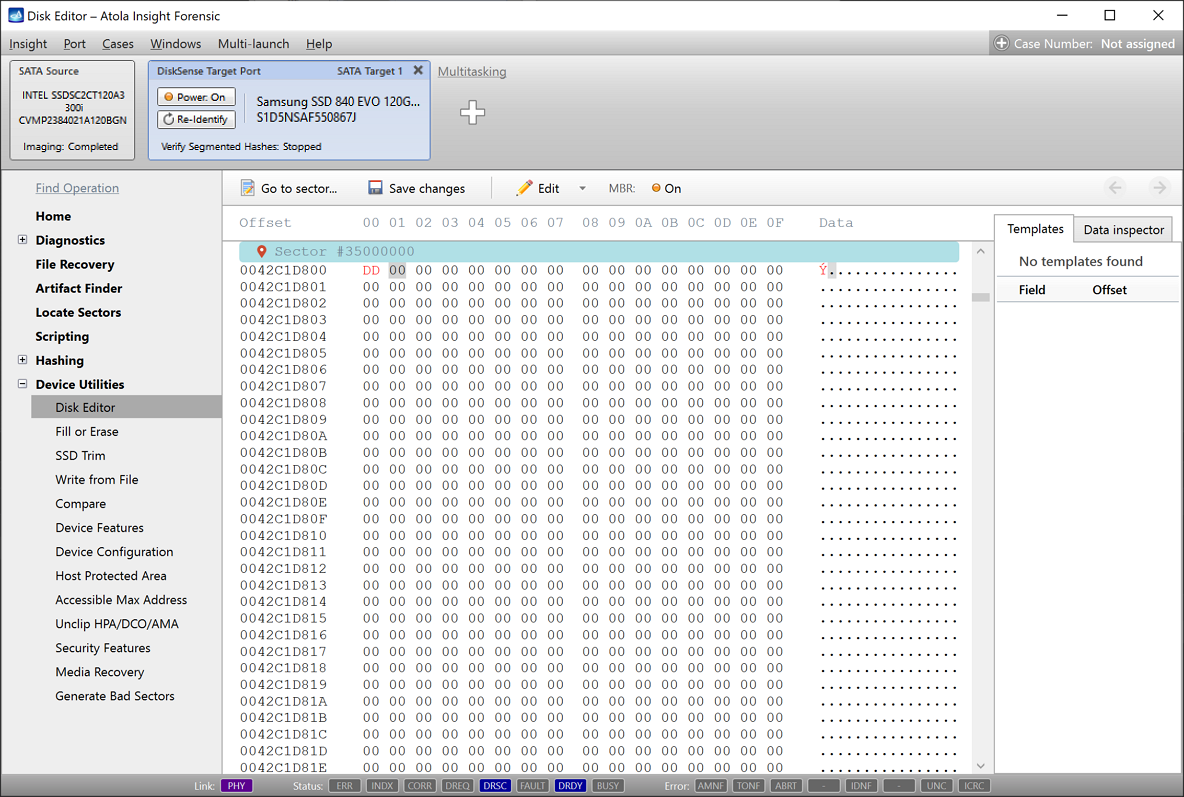
Step 1. In the top Device panel, select the target image. In the sidebar, go to Device Utilities > Disk Editor. Click Go to sector and enter 35,000,000. Change one byte in this sector and click Save changes.
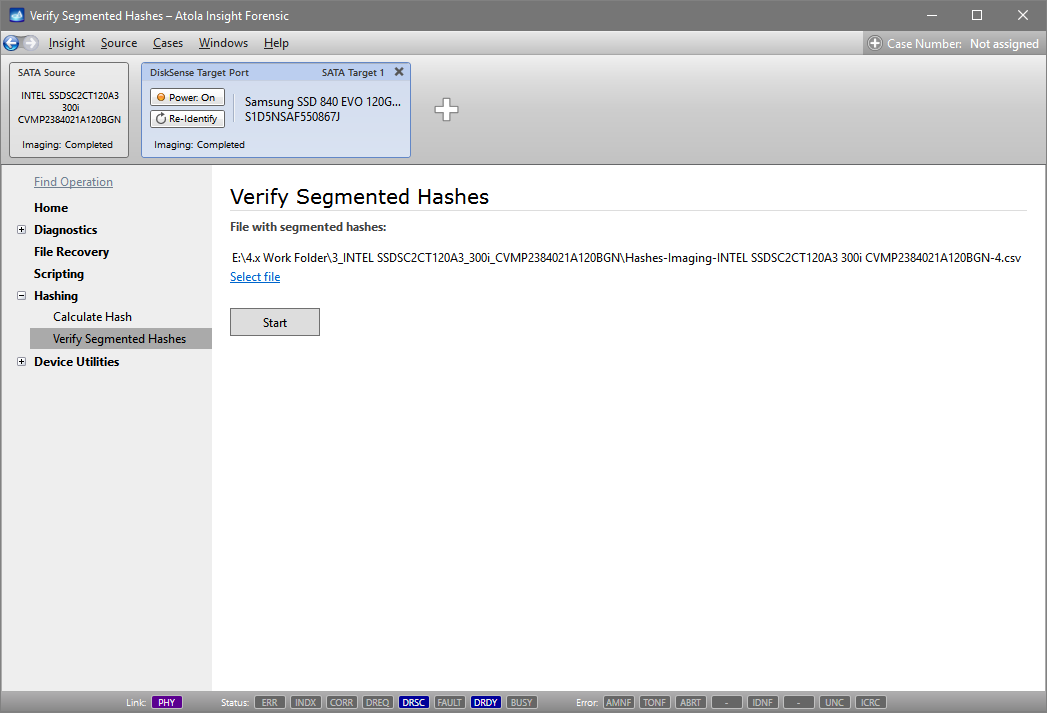
Step 2. In the sidebar, go to Hashing > Verify Segmented Hashes. This is an automated way to verify the segmented hashes in an existing CSV file against the target image. Select the file with segmented hashes calculated during imaging and click Start.
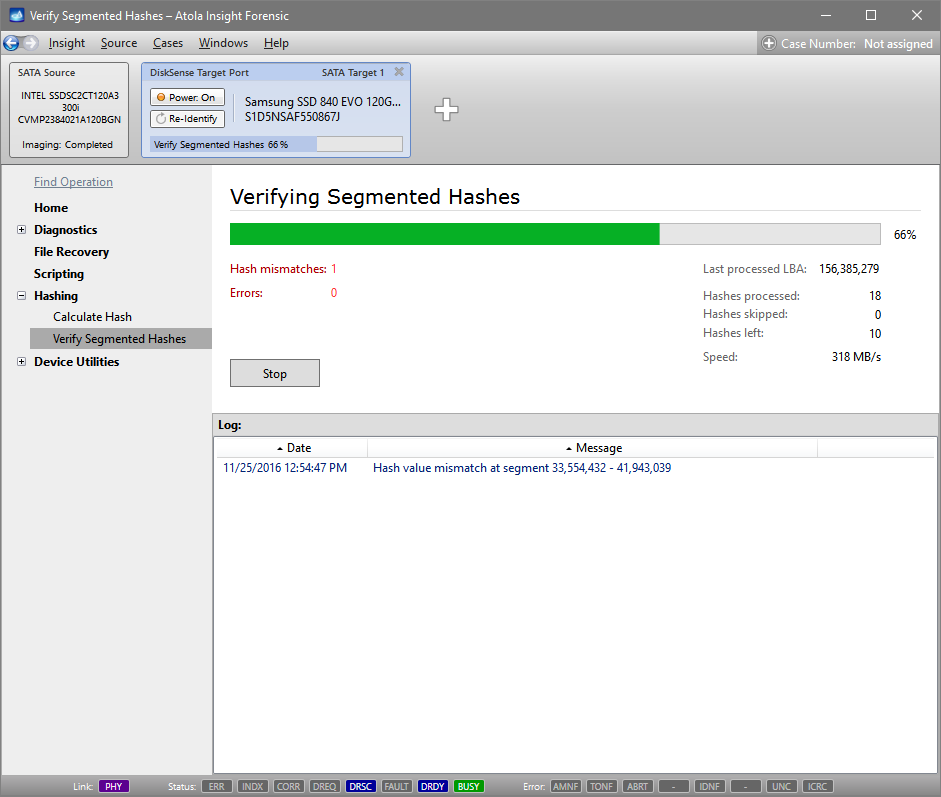
Step 3. Hash verification is in progress. Here we see 18 segmented hashes checked. Hash for the interval that includes sector 35,000,000 is invalid.
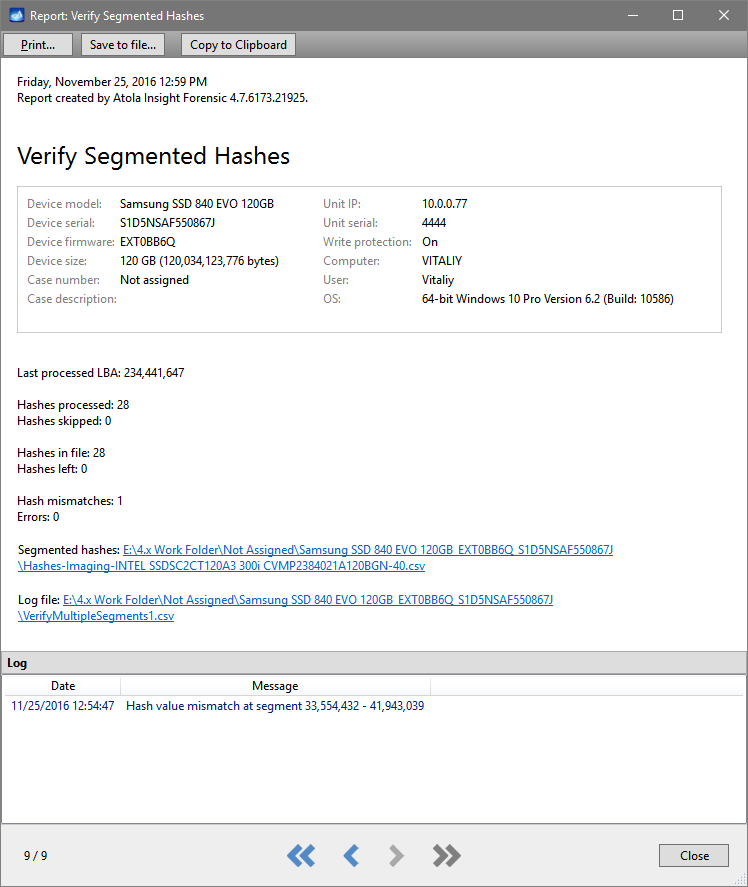
Step 4. Hash verification finishes with the proper case report automatically created, also in CSV format.
This is how segmented hashing helps you avoid the whole image being compromised when a small area of the evidence target is damaged.