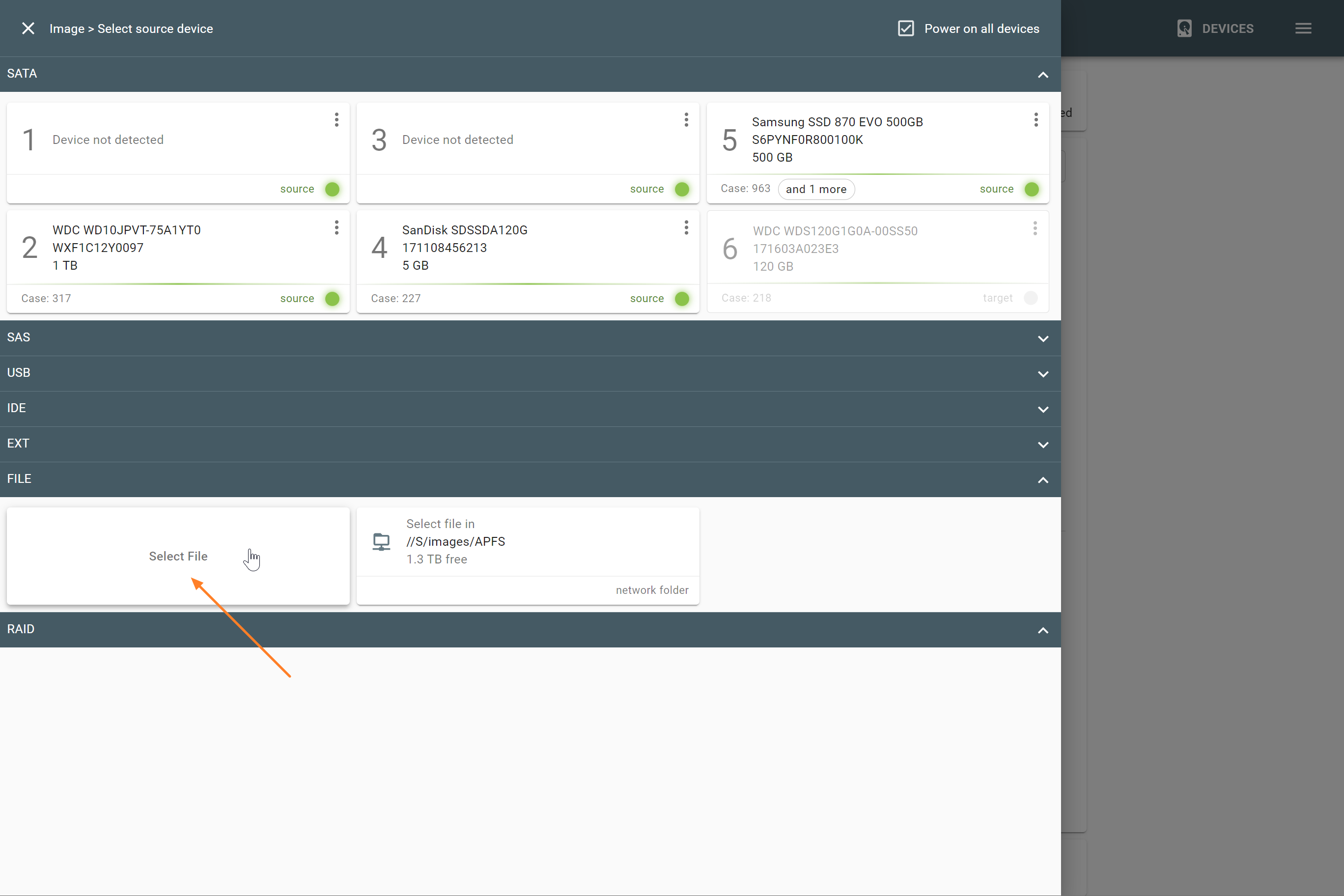
Sources and targets
Atola TaskForce is equipped with 18 configurable ports for all popular drive types and two 10Gb Ethernet ports. Thanks to that it is capable of working with various types of imaging sources and targets.
TaskForce creates a forensically sound bit-by-bit copy of a single drive, RAID array, or forensic file and writes an image to another drive, to a file on a storage device connected to TaskForce, or to a file on a network-connected server.
Available data acquisition types are:
- From a source drive to a target drive directly connected to TaskForce
- From a source drive to file on a storage device directly connected to TaskForce (storage can be encrypted for additional safety)
- From a source drive to a file on a network-connected server
- From an assembled RAID array to a target drive or network device
- From a source forensic file to a drive directly connected to TaskForce
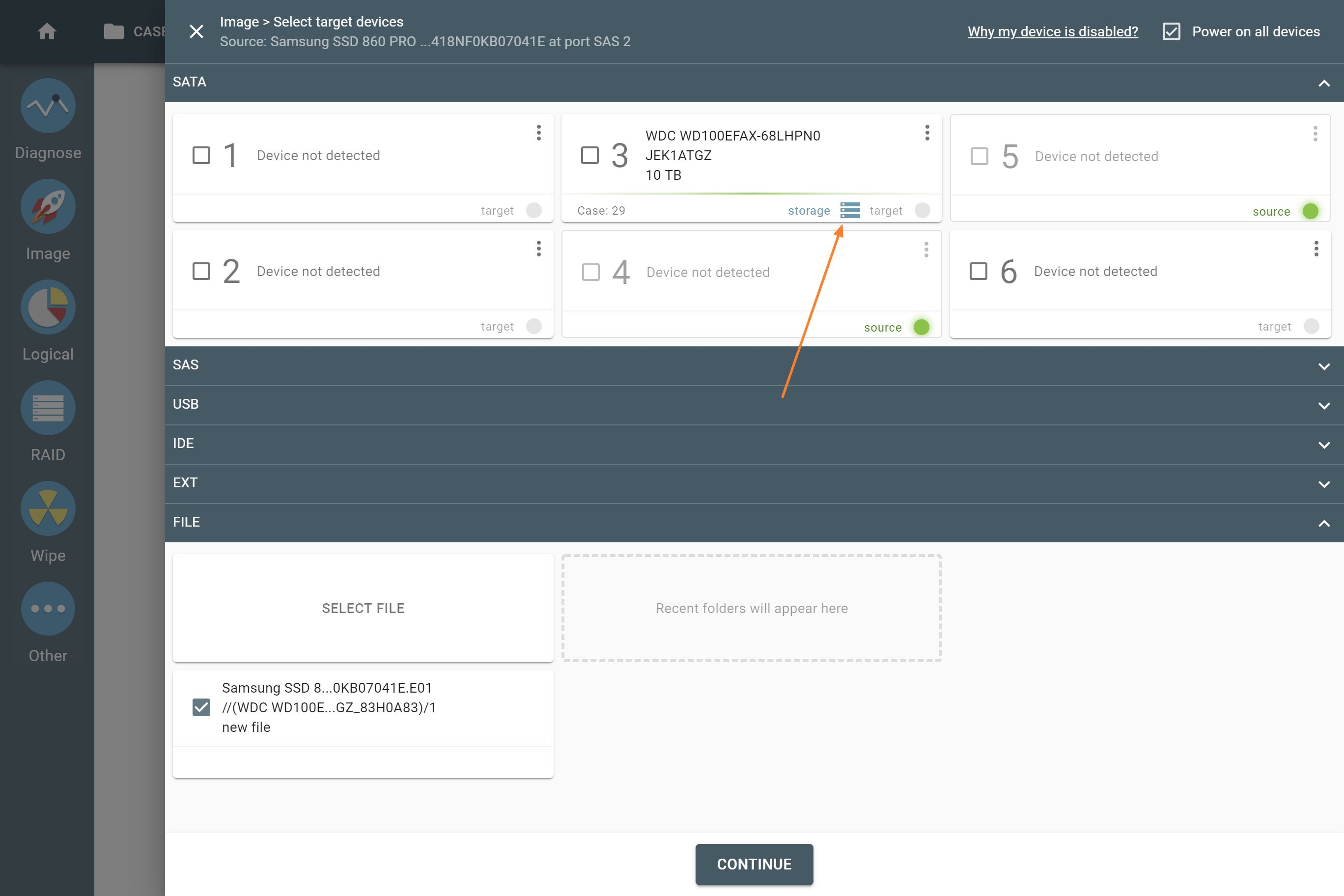
Using TaskForce’s 18 ports, you can image evidence drives of the following types:
- 6 SATA
- 6 SATA/SAS
- 4 USB
- IDE
- Extension port (for Thunderbolt/Firewire, M.2 SSD including NVMe, Apple PCIe SSD devices).
Each of the 18 ports can be used as a source or as a target, depending on your current needs. The port in a source mode enables hardware write protection to guarantee that evidence stays intact.
Image from a source drive to a target drive
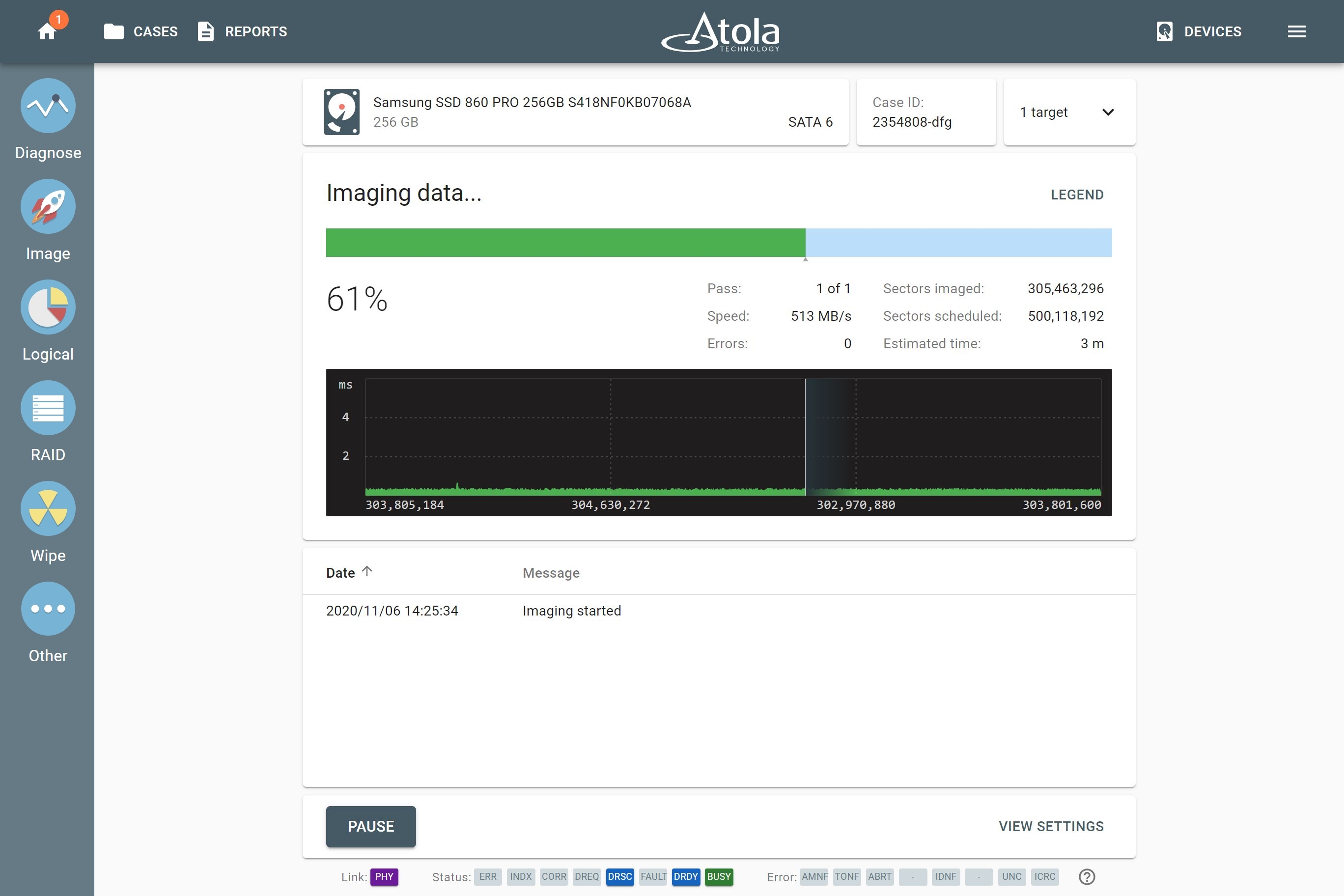
Copy one source drive to up to 5 targets connected directly to TaskForce ports, all at the same time, in a forensically sound manner.
Thanks to TaskForce’s server-grade hardware, it is possible to achieve top native speeds of the drives during the imaging process.
Run up to six SSD-to-SSD imaging sessions or up to nine HDD-to-HDD imaging sessions in parallel, with simultaneous hash calculation, all at the top native speeds of the drives.
Image from a source drive to a file
Save an identical copy of an evidence device as a forensic file on a network server or on a target storage drive, directly connected to TaskForce.
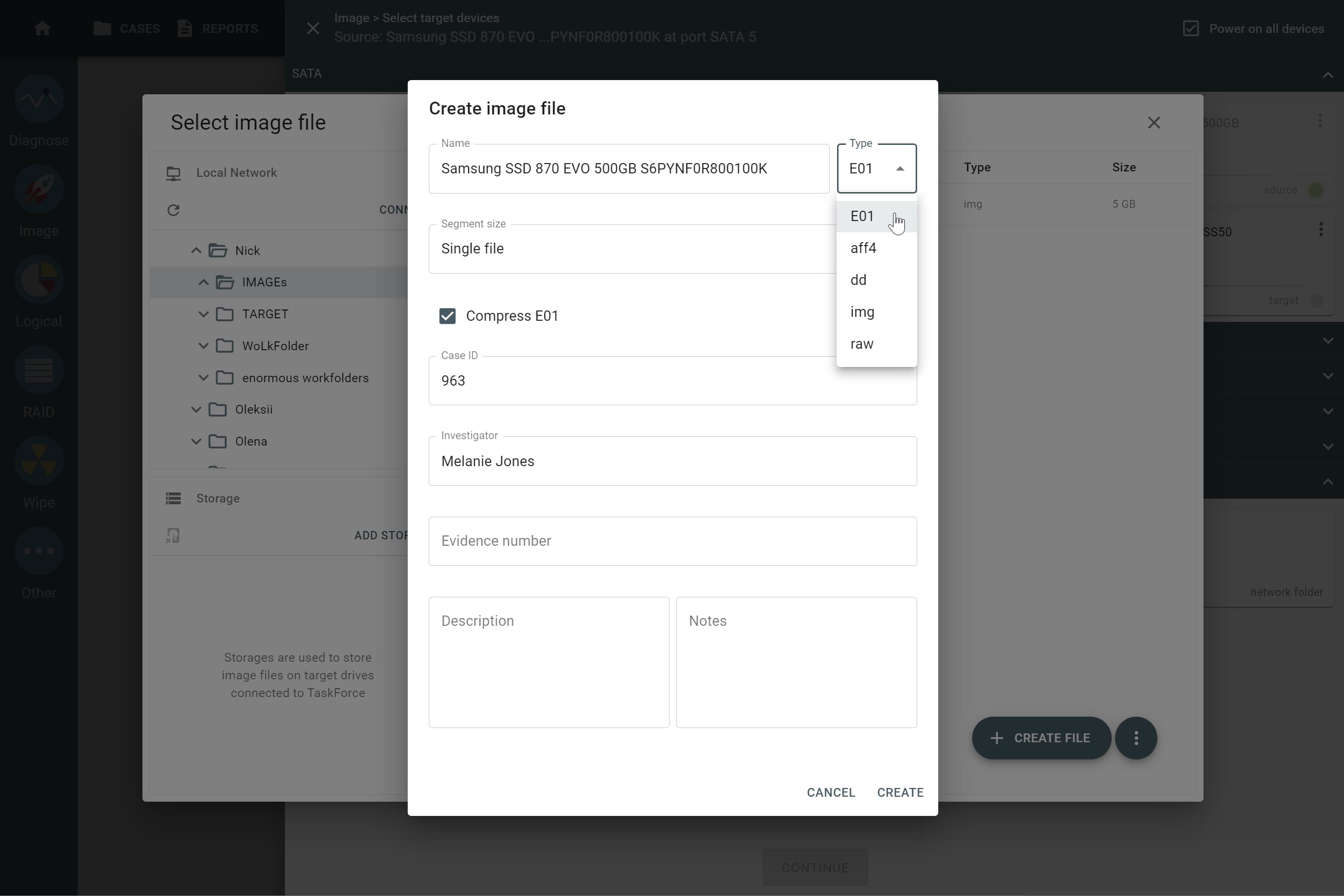
Choose the target type from available forensic file formats:
- E01
- AFF4
- RAW (DD, IMG)
- L01 (in case of logical imaging)
Image from a drive to a file on a network server
For faster imaging from an evidence drive to a file on a network server, set up a 10Gb network and exploit the power of TaskForce’s two 10Gb network ports. Pay attention to other factors that can influence the overall performance when imaging to a network target:
- network speed
- current network workload
- write speed of the server’s drives
To speed up imaging to a network server even more, try using the following target file formats:
- Sparse file. To save both time and space, TaskForce optimizes the copying of sector ranges with binary zeroes. Using the sparse file as a target is available only if the server’s file system supports that file format.
- Compressed file. TaskForce’s highly productive server-grade processor easily compresses chunks of E01 files on the fly. The option is available if the data on the evidence drive is not encrypted.
- RAW file. If you’re dealing with a severely damaged evidence drive, choose this option to get the advantage of the multipass imaging algorithm while avoiding causing further drive damage.
Image from a drive to a file on a directly connected storage drive
Connect a drive directly to TaskForce, configure it to Storage mode, and use it to save multiple target images. To improve performance, before switching the drive to Storage mode TaskForce formats it to an exFAT file system with clusters of 32 megabytes.
For an additional layer of security, a storage drive can be encrypted using VeraCrypt with a 256-bit AES algorithm and locked with your password.
Assemble RAID and image it to a drive or a file
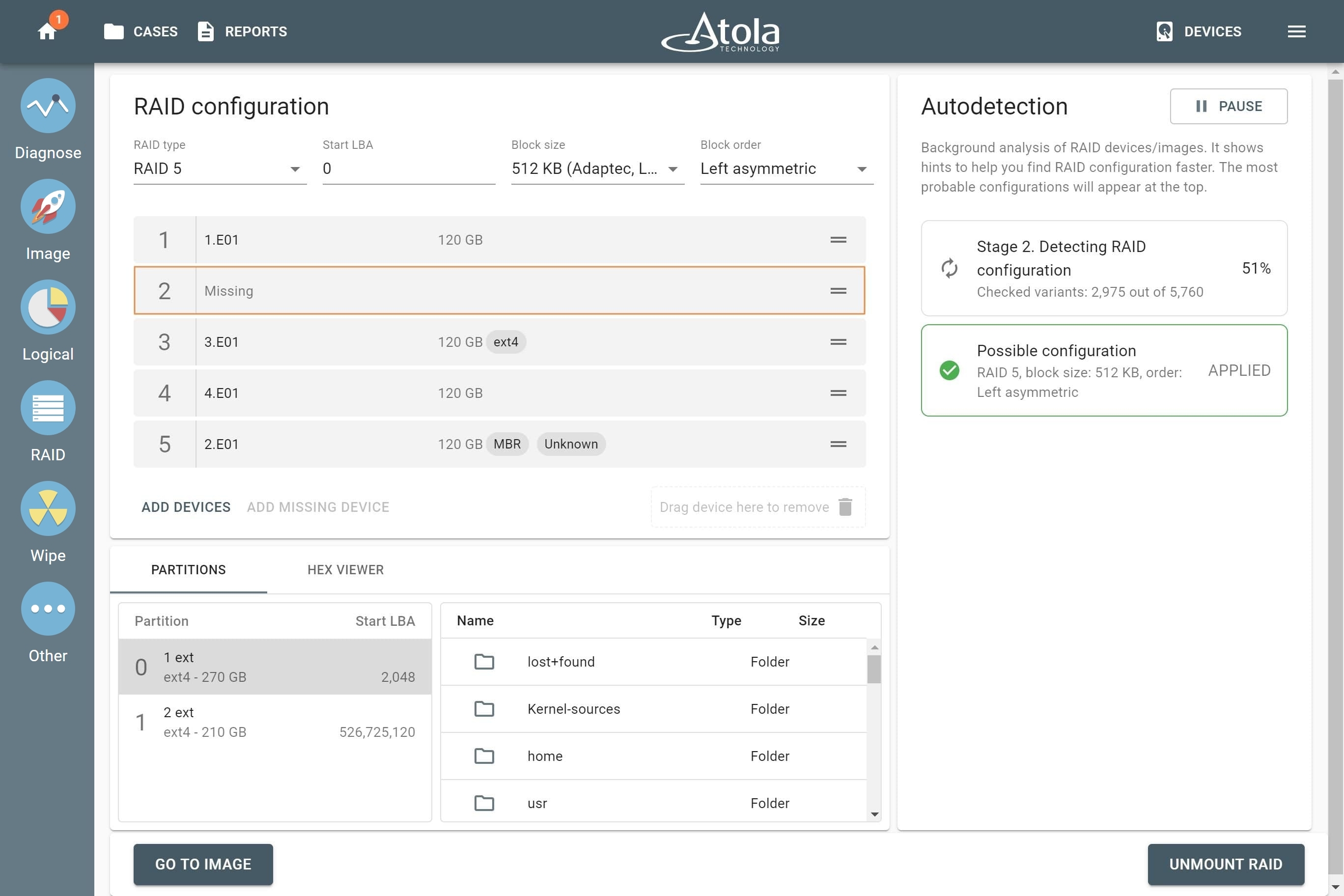
Automatically assemble a bunch of evidence drives or forensic image files (or both) into one functional RAID array. Check its contents and then image the whole array or its selected partitions to a drive or a file.
Reassemble and image RAID 5 even if one of the array’s members is damaged or missing, using RAID 5 redundancy. In that case, TaskForce recreates the missing data by reading corresponding blocks of other RAID drives or parity blocks.
In time-sensitive situations, speed up evidence acquisition by imaging only selected folders and files from a RAID array thanks to the logical imaging module with predefined and customizable filters.
Restore source image from a file to a drive
Using TaskForce, you can restore evidence data from a forensic image file to a physical drive.
The system supports E01, RAW, and AFF4 forensic file formats which can be stored on a network folder, network-attached storage (NAS) device, and encrypted or unencrypted target storage drive directly connected to TaskForce.